Network Authentication Exposed: The Hacker’s Worst Nightmare! What is ethical hacking and how to become an ethical hacker?
If you are searching about Shields Up!! Software Review – Doyle's Space you've came to the right place. We have 25 Pictures about Shields Up!! Software Review – Doyle's Space like 33 million Authy users exposed in authentication app's own security, Cyber Attack Cheat Sheet [Infographic] and also 'Winter' of cyber-threats is coming, experts warn | The Times of Israel. Here it is:
Shields Up!! Software Review – Doyle's Space
 doyletatum.com
doyletatum.com
Shields Up!! Software Review – Doyle's Space
Hackers – A Network's Worst Nightmare
 www.securityri.com
www.securityri.com
Hackers – A Network's Worst Nightmare
33 Million Authy Users Exposed In Authentication App's Own Security
 www.foxnews.com
www.foxnews.com
33 million Authy users exposed in authentication app's own security ...
Hacker Data Security Technology Blue Background, Data Secure Theft
 www.vecteezy.com
www.vecteezy.com
Hacker data security technology blue background, data secure theft ...
Prime Video: Your Worst Nightmare - Season 5
 www.primevideo.com
www.primevideo.com
Prime Video: Your Worst Nightmare - Season 5
Phishing Y La Explotación De Vulnerabilidades, Principales Amenazas En
 directortic.es
directortic.es
Phishing y la explotación de vulnerabilidades, principales amenazas en ...
Hacker Symbol
Hacker Symbol
Issue 209: CSRF In Plesk API-enabled Server, Top Five API Security
 apisecurity.io
apisecurity.io
Issue 209: CSRF in Plesk API-enabled server, top five API security ...
Multi-Factor Authentication (MFA) En Azure AD Y M365 - Guía De
 madsblog.net
madsblog.net
Multi-Factor Authentication (MFA) en Azure AD y M365 - Guía de ...
HACKED! How To AVOID YOUR WORST NIGHTMARE. Meet "Helpful Hacker
 www.youtube.com
www.youtube.com
HACKED! How to AVOID YOUR WORST NIGHTMARE. Meet "Helpful Hacker ...
Pin On My Outfits
 co.pinterest.com
co.pinterest.com
Pin on My outfits
Cyber Attack Cheat Sheet [Infographic]
![Cyber Attack Cheat Sheet [Infographic]](https://infographicjournal.com/wp-content/uploads/2020/04/types-of-cyberattacks-feat.jpg) infographicjournal.com
infographicjournal.com
Cyber Attack Cheat Sheet [Infographic]
Free Hacker Stealing Data Ppt 79229 Sagefox Powerpoin - Vrogue.co
 www.vrogue.co
www.vrogue.co
Free Hacker Stealing Data Ppt 79229 Sagefox Powerpoin - vrogue.co
Messy Pc Room Cables - Recherche Google | Pc Setup, Cool Tech, Messy Room
 www.pinterest.com
www.pinterest.com
messy pc room cables - Recherche Google | Pc setup, Cool tech, Messy room
Good Vs. Bad Hacking — What's The Difference?
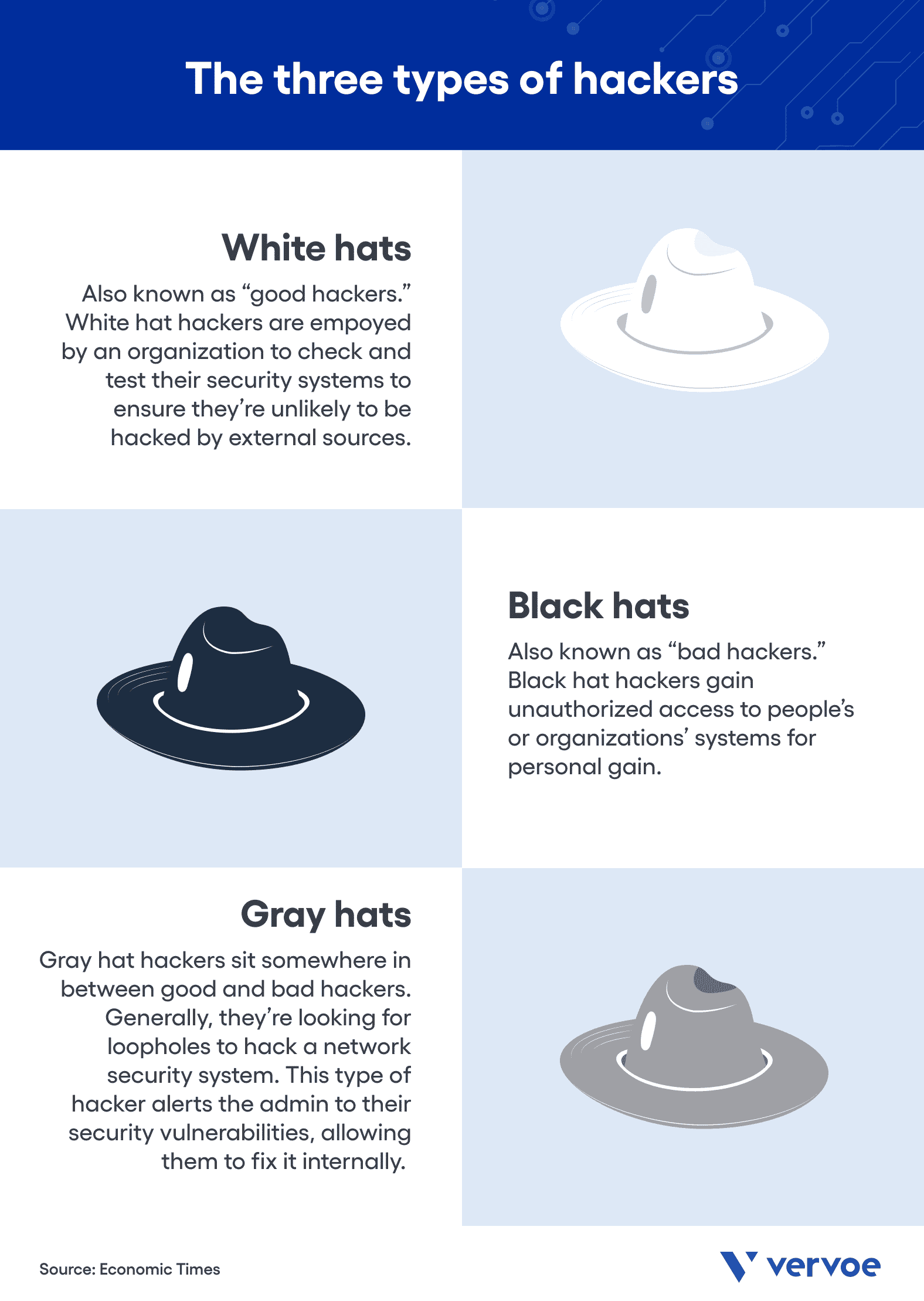 vervoe.com
vervoe.com
Good Vs. Bad Hacking — What's The Difference?
API2:2019 Broken User Authentication: The What, Impact, Sample Exploit
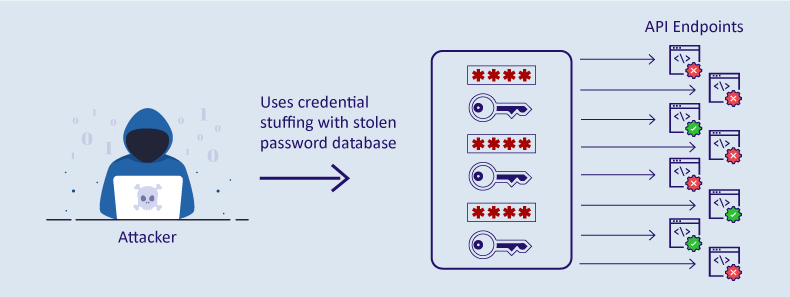 securityboulevard.com
securityboulevard.com
API2:2019 Broken User Authentication: The What, Impact, Sample Exploit ...
Bí Ẩn Sau Cái ᴄʜᴇ̂́ᴛ Của Quý Bình: ᴛʀᴏ ᴄᴏ̂́ᴛ Bị Giam, 30 Tỷ Bảo Hiểm
 www.facebook.com
www.facebook.com
Bí Ẩn Sau Cái ᴄʜᴇ̂́ᴛ Của Quý Bình: ᴛʀᴏ ᴄᴏ̂́ᴛ Bị Giam, 30 Tỷ Bảo Hiểm ...
This VIRUS Is YouTube's Worst Nightmare! - Project Zorgo Hacker Vlog
 www.youtube.com
www.youtube.com
This VIRUS is YouTube's Worst Nightmare! - Project Zorgo Hacker Vlog ...
Hacker, Bad Boy Hacker HD Phone Wallpaper | Pxfuel
 www.pxfuel.com
www.pxfuel.com
Hacker, Bad Boy Hacker HD phone wallpaper | Pxfuel
Silent Network Authentication | Message Central Blog
 www.messagecentral.com
www.messagecentral.com
Silent Network Authentication | Message Central Blog
Multi-Factor Authentication (MFA) Explained
 blogs.truststamp.ai
blogs.truststamp.ai
Multi-Factor Authentication (MFA) Explained
What Is Ethical Hacking And How To Become An Ethical Hacker?
 freeservermonitor.com
freeservermonitor.com
What is Ethical Hacking and How to Become an Ethical Hacker?
'Winter' Of Cyber-threats Is Coming, Experts Warn | The Times Of Israel
 www.timesofisrael.com
www.timesofisrael.com
'Winter' of cyber-threats is coming, experts warn | The Times of Israel
The Different Types Of Hacking Techniques Explained: A Helpful Guide
 www.sdgyoungleaders.org
www.sdgyoungleaders.org
The Different Types of Hacking Techniques Explained: A Helpful Guide
Cyber War: I Hate Hackers • The Havok Journal
 havokjournal.com
havokjournal.com
Cyber War: I Hate Hackers • The Havok Journal
'winter' of cyber-threats is coming, experts warn. Pin on my outfits. Bí ẩn sau cái ᴄʜᴇ̂́ᴛ của quý bình: ᴛʀᴏ ᴄᴏ̂́ᴛ bị giam, 30 tỷ bảo hiểm